OpenVPN with LDAP + 2-Factor Authentication and Network Access Polices
Contents
Contents
Introduction
This blog post will explain the steps taken to configure OpenVPN to authenticate users using LDAP authentication and 2-Factor authentication. LDAP authentication will be performed against Active Directory, and 2-Factor authentication will be performed with a Time-based One-Time password (TOTP). Furthermore, the network access of users will be restricted to only what the administrator wants them to access.
This post is split up into 5 sections:
- VPN Server Initial Configuration
- Base OpenVPN Configuration
- Configuring LDAP Authentication
- 2-Factor Authentication with TOTP
- User Based Network Access Polices
The first section will configure the server on which the VPN server will be setup on. Next, OpenVPN itself will be setup without any authentication. After LDAP authentication will be configured against Active Directory. Then 2-Factor authentication will be added. Lastly, network access polices will be configured for each user.
The first two sections are required in order to have a functioning OpenVPN server, the third section is required in order to have authentication on the OpenVPN server. The fourth section will add additional authentication. And the last section will be used to authorize users to specific services on a network. If you want, you can only work up to the third section if you do not need 2-Factor authentication or network based access polices.
The following picture shows the flow of the whole process.
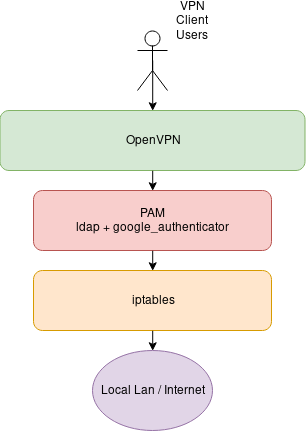
VPN Server Initial Configuration
In this section the prerequisite server configurations will be performed on the server that will host OpenVPN.
The following versions of software:
- CentOS 7.6.1810
- OpenVPN 2.4.7
- EasyRSA 3.0.6
Begin by updating the server.
|
|
Next disable firewalld. Instead iptables will be used.
|
|
Install the iptables service in order to keep iptables rules on boot.
|
|
There are some default iptables rules, clear everything and save them. Configuration of firewall will be done at a later time.
|
|
Install the Fedora extended repository which contains OpenVPN.
|
|
Install OpenVPN.
|
|
Install wget for later
|
|
Install your favorite text editor, it does not have to be Vim.
|
|
Base OpenVPN Configuration
In this section OpenVPN will be configured with a CA and certificate. It will be setup to accept any username and password combination in order to confirm that it is running and operating as it should.
Setting up Certificate and CA for VPN Server
Begin by downloading EasyRSA . This software will be used to create a CA along with key and certificate for the OpenVPN server.
|
|
Enter the extracted EasyRSA folder.
|
|
Copy the EasyRSA configuration file, and enter it using vim (or another editor).
|
|
Uncomment following lines which will enable the use of RSA with 2048 bits. There is also an option to use elliptic curves.
|
|
Create the CA, VPN key, certificate, and Diffie Hellman parameters.
|
|
Copy needed files to root of OpenVPN configuration directory. The files being copied are the CA certificate, Diffie Hellman parameters, VPN server certificate, and VPN server key.
|
|
The following shows all the files that where copied.
|
|
Creating OpenVPN config
Create file located at /etc/openvpn/server.conf and add the following configurations.
|
|
SELinux Issues
NOTE: If you are using SELinux and wish to run OpenVPN on a nonstandard port, it will not let you. If you do not have SELinux, than this section does not apply to you. If you do wish to run on a nonstandard port, please follow the following.
Install policycoreutils-python package and use semanage to see what ports are allowed.
|
|
You can add another port using the following command:
|
|
Setting up PAM
This section will setup PAM authentication that OpenVPN will use, however, we will not have any actual users or LDAP authentication. This will be to make sure that the VPN server is capable of starting up properly and that the client side can connect.
Create a file /etc/pam.d/openvpn and add the following to it. This allows anyone to authenticate with any credentials.
|
|
Starting OpenVPN
Start OpenVPN
|
|
If you encounter any errors, consult /etc/openvpn/openvpn.log.
Testing Client Connection
The following is the client configuration needed to connect to OpenVPN. Create this file on a different computer from the server. Do not forget to replace X.X.X.X with the IP address of your VPN server.
|
|
Another component that is needed is the CA certificate located at /etc/openvpn/ca.crt. Copy this file to the client computer in the same directory as the client configuration.
When the OpenVPN client asks you for a username and password, type anything. Any credentials will be accepted, we are doing this to make sure that the OpenVPN server is properly working and that we can connect to it.
If the client can successfully connect to the server then everything is working.
Configuring LDAP Authentication
In this section LDAP authentication will be setup. This authentication will be performed against Active Directory, only users that are apart of a security group named vpngroup will be allowed to authenticate.
Active Directory Setup
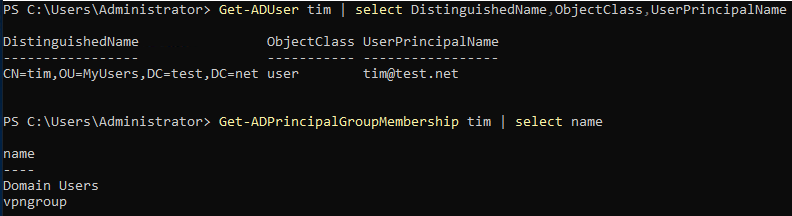
As can be seen below there is an OU named MyUsers. Inside we have two users named tim and vpnbind, and a security group named vpngroup.
The vpnbind user account will be used to access LDAP from the VPN server.
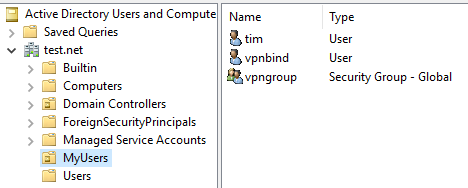
The tim user account will be our VPN user, this user is apart of the vpngroup security group in order to have vpn access.
LDAP Service Setup
Install the LDAP PAM module.
|
|
Paste the following into /etc/nslcd.conf. This is a deamon that will run in the background, its job is to perform LDAP queries on behalf of another process.
|
|
Start the nslcd service.
|
|
Configure PAM that is used by OpenVPN
Paste following into /etc/pam.d/openvpn. Only the first line is changed from what was before.
|
|
Testing LDAP Authentication with OpenVPN
Restart OpenVPN server.
|
|
Now use the same client configuration from last time to connect as a domain user. If you are not planning on adding 2-Factor authentication or network access polices, skip here in order to configure VPN network connectivity.
2-Factor Authentication with TOTP
This section will configure TOTP based 2-Factor authentication using Google Authenticator. The Google Authenticator or andOTP mobile application can be used to view the codes.
Begin by installing Google Authenticator.
|
|
Create a new folder in the root of OpenVPN configuration which will store the shared secret between the server and user.
|
|
Alter the PAM configuration for OpenVPN in /etc/pam.d/openvpn to include Google Authenticator.
|
|
Create a OTP setting for a user.
|
|
After running this command scan QR code with app.
Please note that as the OTP expires the renegotiation time must be set to 0 so the user does not get disconnected, of course this can also be used as a mechanism to timeout the users connection if one wishes.
In order to disable renegotiation set the following in /etc/openvpn/server.conf and user config.
|
|
SELinux Issues
NOTE: If using SELinux you will have to change the file context of the files in
/etc/openvpn/otp. In this example run the following command.
|
|
Testing Two Factor Auth
Restart OpenVPN server
|
|
Connect as the client once again. If your domain password is mypassword and your OTP code is 123 456 enter the password as mypassword123456.
Configuring Network Access
Now that the user can successful authenticate and connect to OpenVPN we will configure forwarding and firewall polices so the users can access either the internal network or internet.
Turn on forwarding
|
|
Set up outgoing NAT. Be sure to change the source subnet to what was set in the OpenVPN server configuration.
|
|
At this point any user that connects will be able to connect to the local LAN network that the VPN server is on. A small configration change must be made in order to redirect all the traffic of the client through the VPN server.
Don’t forget to save the iptables rules:
|
|
In /etc/openvpn/server.conf comment out the following:
|
|
And uncomment the following:
|
|
Now restart the VPN Server
|
|
User Based Network Access Polices
In order to regulate the network activity of each user iptables will be used. The issue is that we cannot predict which IP address a user will receive. In order to combat this a static IP address will be given to each user.
As our tunnel network we are using 10.8.0.0/24, we will split this into two subnets. One subnet will be for Administrators and the other for users.
| User Type | Subnet |
|---|---|
| Admins | 10.8.0.0/25 |
| Users | 10.8.0.128/25 |
Furthermore, in this example we will have the following users.
| Username | Static IP |
|---|---|
| Tim | 10.8.0.100/25 |
| Bob | 10.8.0.200/25 |
Assigning Static IP address
Create the client configuration directory
|
|
Now we will create two files in /etc/openvpn/ccd
Add the following into the file /etc/openvpn/ccd/tim.
|
|
Add the following into the file /etc/openvpn/ccd/bob.
|
|
Also make sure to uncomment or add the following line in /etc/openvpn/server.conf.
|
|
Now restart the VPN and each user should be getting a static ip on connect
|
|
Firewall Polices
The following iptables configuration will create two chains, ADMINS and USERS. When an IP address falls into a specific subnet it will be sent to the corresponding chain. Any rules you wish to enforce on the users can be added into the chains.
|
|